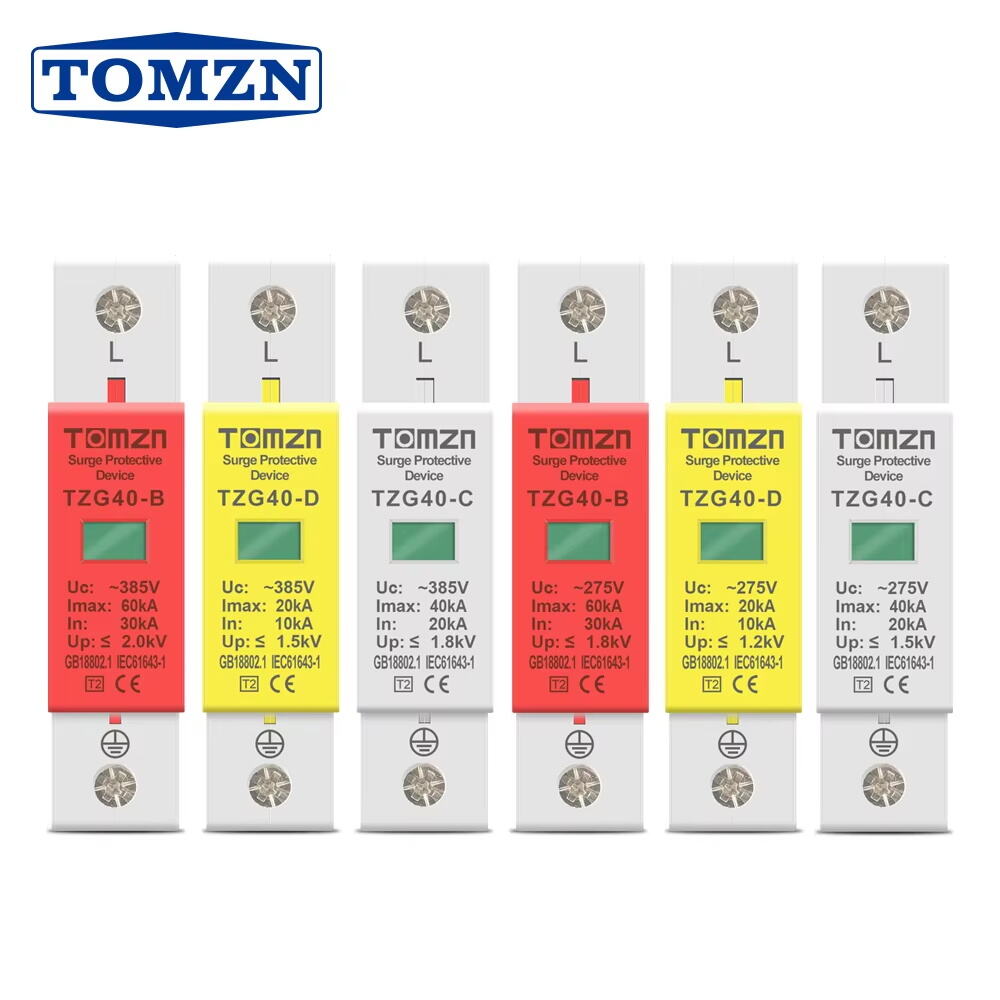
wifi protector vendors
WiFi protector vendors play a crucial role in modern cybersecurity by providing comprehensive solutions to safeguard wireless networks and connected devices. These vendors offer specialized software and hardware solutions designed to detect, prevent, and neutralize various cyber threats targeting WiFi networks. Their products typically include advanced encryption protocols, real-time threat monitoring systems, and intrusion detection capabilities. These solutions employ sophisticated algorithms to identify suspicious activities, unauthorized access attempts, and potential security breaches. The vendors also provide regular updates to their security databases, ensuring protection against emerging threats and vulnerabilities. Many solutions incorporate machine learning capabilities to adapt to new attack patterns and improve threat detection accuracy over time. These systems often feature user-friendly interfaces that allow both technical and non-technical users to monitor network security status, manage connected devices, and implement security policies. Additionally, WiFi protector vendors frequently offer cloud-based management platforms, enabling remote monitoring and control of multiple network security systems across different locations. Their solutions typically include features such as virtual private network (VPN) integration, firewall protection, and secure guest network management capabilities.